 FCA and PRA licenses (authorisations) and ongoing compliance support, training, recruitment. Contact us 7 days a week, 8am-11pm. Free consultations. Phone / Whatsapp: +4478 3368 4449 Email: hirett.co.uk@gmail.com
FCA and PRA licenses (authorisations) and ongoing compliance support, training, recruitment. Contact us 7 days a week, 8am-11pm. Free consultations. Phone / Whatsapp: +4478 3368 4449 Email: hirett.co.uk@gmail.com
PART A. PREAMBLE
1. PURPOSE AND SCOPE
1.1 Hirett is a Money Transfer / Money Exchange business. It is important to Hirett to be able to identify, report and take precautions to guard against money laundering. We are required to abide by anti-money laundering (AML) legislation, which applies to all of our activities, and we have a duty to safeguard customers money. It is the policy of Hirett to prohibit and actively prevent money laundering and any activity that facilitates money laundering or the funding of terrorists or criminal activity.
1.2 We focus on developing a culture where the highest priority is given to ensure compliance with government regulations. This is helped by regular staff training to make sure they are aware of the law and their responsibilities.
1.3 We recognize that it is a legal requirement for us to notify the regulatory authorities whenever it has suspicions of any criminal activity by individuals engaged in a money transfer / foreign currency transaction.
1.4 The outcomes sought from this policy, then, are that:
• We meet anti-money laundering legal requirements
• Staff are aware of and understand the AML requirements, offences and background and the process and expectations set down in this policy – and appropriate support is in place to ensure it is complied with
• We have a robust, risk-based process, which is effectively and consistently followed, to understand with whom we are dealing and any money laundering risks
• We maintain comprehensive records of anti-money laundering checks and concerns
• Money laundering suspicions are proactively and immediately reported, and ultimately, we guard against Hirett becoming involved in money laundering
• safeguarding customers funds
SCOPE
1.5 Hirett’s AML policy applies to all of its staff and agents using Hirett system to Transmit money.
1.6 This policy also set rules for Currency Exchange related services – it applies to everyone at the Hirett: you must ensure you comply with the legislation and this policy.
HIRETT’S WIDER GOVERNANCE ARRANGEMENTS
1.7 The AML Policy is part of Hirett’s anti-money laundering framework, including its Risk Assessment on all business area’s and other security, IT and data protection policies should be read alongside this document.
2. CORE RESPONSIBILITIES AND CORPORATE REQUIREMENTS
RESPONSIBILITIES
2.1 THE DIRECTOR – The Director has direct responsibility for compliance with AML/CTF legislation and directives globally. Money laundering is the number one risk to the business and must have sufficient time devoted to its prevention and protection. The Director must ensure that the person appointed to the role of Compliance Officer is suited to its requirements and responsibilities, and that adequate resources are available to them to fulfil the business’ AML policy requirements. These requirements include accreditation, training, transaction monitoring, and compulsory reporting and recording.
The work of the Compliance Officer needs to be fully understood and supported by the Board, in this case the director himself. It is therefore necessary that he/she has a comprehensive knowledge of the work involved and actively reviews the output of the Compliance Officer. It is the director’s responsibility to ensure that adequate procedures and processes are in place to meet business- specific Anti Money Laundering
Compliance requirements.
2.2 COMPLIANCE OFFICER – Hirett have a dedicated resource, an independent compliance officer, responsible for the AML/CTF program and its supervision – the Compliance Officer – this resource shall maintain overall responsibility.
For Hirett the Compliance Officer, Mr. John Jacobs is the appointed Money Laundering Reporting Officer and Nominated Officer for the Company.
AML COMPLIANCE OFFICER DUTIES:
2.2.1 According to the MLR Regulations, the Company designates the above named person as the Anti-Money Laundering Program Compliance Officer, with full responsibility for the Company’s anti-money laundering (AML) program.
2.2.2 The Compliance Officer responsibilities includes but not limited to, know your Agent, know your Customer review, transaction monitoring, reporting, dealing with Law Enforcement requests, risk assessment, training and the review of procedures and policies. This covers the review of this AML/CTF Policy & Procedure Manual at least annually.
The MLRO must:
• Receive and consider internal disclosures of suspected money laundering or terrorist financing;
• Decide whether there are sufficient grounds for suspicion to pass the disclosures to NCA;
• File a suspicious activity report (SAR) with NCA where the grounds for suspicion are sufficient; and
• Liaise with NCA to deal with such matters as consent to proceed with a transaction and other disclosure issues, particularly with regards to clients or third parties.
• The MLRO will also ensure that proper AML records are kept. When warranted, the MLRO will ensure Suspicious Activity Reports are filed with the NCA.
2.3 AGENTS & EMPLOYEES – All management level employees and Agents, regardless of their responsibilities within the business, are to be trained at least annually. This training is conducted by the Compliance Officer or the compliance Trainer.
REQUIREMENTS
3. SAFEGUARDING
3.1 Hirett is fully aware of its obligation of safeguarding of funds as stated within the Electronic Money Regulations 2011 (EMRs) and Payment Services Regulations 2017 (PSRs).
RESPONSIBILITY:
3.2 The obligation to safeguard starts immediately on receipt of funds (‘relevant funds’).
3.3 The purpose of safeguarding is to protect customers funds held by an institution. They do this by ensuring that those funds are either placed in a separate account from the institution’s working capital and other funds, or are covered by an appropriate insurance policy or comparable guarantee.
3.4 In case of the insolvency of an institution, claims of e-money holders or payment service users are paid from the asset pool formed from these funds in priority to all other creditors (other than in respect of the costs of distributing the asset pool).
HOW WE COMPLY WITH DUTY?
3.5 The objective of the safeguarding rules is to consider what would happen to our client’s funds in the unlikely event that our firm went into administration.
3.6 When we receive funds in relation to a trade, the money is received into a client bank account. Those client accounts are not commingled with firm money and in the unlikely event of administration, no other creditors can have access to these funds. We conduct daily reconciliations to ensure that the client balances as per our internal records corresponds to the funds held in the client accounts.
PART B. SANCTIONS AND LEGISLATIONS
4. WHAT IS MONEY LAUNDERING?
4.1 The Money Laundering Regulations require a fundamental understanding of the processes that can be involved in money laundering, and require that you respond appropriately to any knowledge or suspicions that these processes may be taking place. This section of the policy explains what money laundering is, the offences and the penalties.
4.2 Money laundering is any process whereby funds derived from criminal activity including terrorist financing are given the appearance of being legitimate by being exchanged for ‘clean’ money.
4.3 Participating in the handling of such funds is illegal, and it can also be illegal to become involved in them with knowledge or suspicion.
For Example: Money transmission can involve placing illegal cash with a money service business, or enabling the transfer of value by netting-off transactions in different countries without moving any money. A common practice is to split transactions into small sums, or to deposit cash into somebody else’s bank account, or to make a transfer of funds on behalf of somebody else
4.4 Currency Exchange businesses are exploited to change small denomination notes into large denominations in another currency to enable easier and cheaper handling of large quantities of illegal cash – once the money has been exchanged, it’s difficult to trace its origin.
4.5 In basic terms, the criminal wants to:
• Place money in the financial system, without arousing suspicion;
• Move money around, often in a series of transactions crossing multiple jurisdictions, so it becomes difficult to identify its original source, and then;
• Move the money back into the financial and business system, so that it appears as legitimate funds or assets.
• Money transmission can involve placing illegal cash with a money service business, or enabling the transfer of value by netting-off transactions in different countries without moving any money. A common practice is to split transactions into small sums, or to deposit cash into somebody else’s bank account, or to make a transfer of funds on behalf of somebody else
4.6 Money laundering involves three stages:
• PLACEMENT – Placement is the first stage of the money laundering process. The aim of this process is to introduce the unlawful proceeds, aka “dirty money”, into the financial system without attracting the attention of financial institutions or law enforcement.
Placement techniques often include structuring (dividing large amounts of currency into less conspicuous smaller sums) currency deposits into amounts
• LAYERING – Layering is the second stage of the money laundering process. It is the process by which the proceeds of illegal activities, i.e. the “dirty money”, is separated from its origins. It is done by moving funds around the financial system through a series of transactions. Create confusion and complicate the audit trail by making numerous transactions; these transactions may reasonably appear to have a legitimate purpose or may appear to have no reasonable, lawful purpose.
• INTEGRATION – Integration is the third step of the money laundering process. It may be performed individually or in conjunction with the Placement and Layering stages. Once the origin of the funds has been hidden through sufficient ‘layering’, the funds are imported back into the financial system.
4.7 Being involved in any of these three stages is potentially a criminal activity.
5. TACKLING MONEY LAUNDERING
CATCH is a shorthand way to remember this and it means:
1. Confirm the identity of each customer
2. Appoint a MLRO
3. Train all staff processing money transfers
4. Control the business by having anti-money laundering system in place
5. Hold all records for at least 5 years
6. WHAT IS TERRORIST FINANCING?
6.1 A person or an entity commits an offence of Terrorist Financing if they;
• fund-raise or are involved in fund-raising, using or possessing money or other property for the purposes of terrorism
• conceal, transfer or remove from jurisdiction, any money or other property used to finance terrorism
• facilitate the retention or control of money, which is destined for, or is the proceeds of terrorism
• do not comply with a prohibition imposed by a freezing order or enable any other person to contravene the freezing order
• deal with, or make available funds or economic resources which are owned, controlled by or benefitting a designated person (under the Office of Financial Sanctions Implementation List)
6.2 Hirett have systems in place to help identity prevent and detect money laundering and terrorist financing.
6.3 Hirett always ensure that its policies, procedures and controls are implemented and kept up to date.
7. LEGISLATIVE REFERENCES
7.1 The relevant legislation includes the latest versions of:
• Proceeds of Crime Act 2002 – This defines the money laundering offences and gives law enforcement agencies far reaching powers to deal with them.
• The Proceeds of Crime Act also creates offences of failing to make a report about suspicious activity, and tipping off any person that you’ve made, or intend to make, such a report. This applies to nominated officers and employees of businesses in the regulated sector, such as money service businesses.
• Money Laundering Regulations 2007 – These regulations set out the detailed requirements for organisations and individuals engaged in regulated activities.
• Terrorism Act 2000 – This defines the primary offences related to terrorist funding and requires regulated businesses to report knowledge or suspicion of offences.
• The Money Laundering, Terrorist Financing and Transfer of Funds (Information on the Payer) Regulations 2017 (referred to in this guidance as “the Regulations”) – make important amendments to the Proceeds of Crime Act, the Terrorism Act and the Anti-terrorism Crime and Security Act. It extends the powers of law enforcement to seek further information, recover the proceeds of crime and combat the financing of terrorism.
• Terrorist Asset-Freezing etc. Act 2010 – The Terrorist Asset-Freezing etc. Act 2010 gives HM Treasury power to freeze the assets of individuals and groups reasonably believed to be involved in terrorism, whether in UK or abroad, and to deprive them of access to financial resources.
• Anti-terrorism, Crime and Security Act 2001 – is to ensure the security of dangerous substances that may be targeted or used by terrorist and allows for freezing orders to be made against national security threats and the civil asset seizure regime for terrorism.
• Counter-terrorism Act 2008, Schedule 7 – gives powers to HM Treasury to issue directions to firms in the financial sector in relation to customer due diligence, ongoing monitoring, systematic reporting and limiting or ceasing business.
8. OFFENCES
OFFENCE and NOTES
| OFFENCE | NOTES |
| Concealing, disguising, converting or transferring illicit funds or removing such funds from the UK | |
| Entering into or becoming concerned in arrangements which it is known or suspected will facilitate the acquisition, use or control of illicit funds by or for another person | |
| Acquiring, using and / or possessing illicit funds | It is possible the Hirett and its employees could unwittingly commit these offences if the Hirett or its services were used by third parties to clean-up money received as proceeds of crime |
| Failure to disclose knowledge or suspicion of money laundering to the Money Laundering Reporting Officer (MLRO) where such knowledge or suspicion is gained (or should reasonably have been gained) through the course of business | This offence can be committed by a failure to report a suspicion of money laundering where, based on the information available to the employee, they should reasonably have held such a suspicion.
You can be guilty of an offence even if you were not suspicious or were not aware of money laundering, if a reasonable person would have been suspicious or aware. This is why it is so important that you read through this policy and the examples given in it. Although the examples are not exhaustive, if you come across anything that is similar to any of these examples, or which seems out of the ordinary, you must speak to the MLRO immediately, even if you are not suspicious yourself. (See PART F, below regarding your reporting obligations.) |
| ‘Tipping off’, which means informing a suspect or third party that a report of suspicion of money laundering has been made to the National Crime Agency (NCA) or to our MLRO or that the suspect is being investigated | The offence of tipping off is committed under the legislation only when a disclosure (ie. a report) to the NCA or MLRO has been made or is contemplated, not before. So, although you must exercise caution, you must still ask appropriate questions at the outset of the transaction to ensure you understand who we are transacting with and to complete the required due diligence (See PART D, below regarding your CDD obligations).
If you become suspicious of money laundering and make a report to the MLRO, it is important from the date of that report you only speak to the MLRO and your line manager about any concerns. You can then discuss with the MLRO what you can say to the people about whom you have suspicions so they are not tipped off that you are concerned. |
| Doing anything that constitutes an attempt, conspiracy or incitement to carry out money laundering or to aid, abet, counsel or procure money laundering to occur. This is the case regardless of whether the act took place within the UK or outside the UK, so we still need to be aware of potential criminal activity where we are involved in transactions involving off-shore entities. This includes any person who knowingly prejudices an investigation into potential money laundering or provides misleading information | Money laundering is often complex and sophisticated so that the proceeds of crime are distanced from the original criminal.
To protect Hirett – and you – from being found guilty of an offence, it is important you comply with this AML Policy in all your transactions involving Money Transfer / Currency Exchange, even if you consider that the potential recipient would not be directly committing a money laundering offence. This is especially the case because illicit funds are defined widely enough to catch involvement with ‘regulatory’ issues which are criminal in nature. For example, a failure to pay stamp duty land tax, a failure to provide source of funds or explanation of origin of funds. You should discuss any such concerns with the MLRO. |
9. PENALTIES
9.1 All the offences listed above are criminal offences and committing them is punishable by prison sentences and/or a fine. For example, if found guilty of the offence of tipping off an individual may be imprisoned for up to two years and may receive a fine of an unlimited amount.
9.2 You should note that offences can be committed by staff as individuals even if you are acting in the course of your employment or as an agent of the business.
9.3 Any failure by a member of staff or an agent to follow this AML Policy, whether relating to a criminal offence or not, by may lead to disciplinary action being terminated employment or immediately ceasing the business relationship with an agent.
10. DEFENCES
10.1 There are certain defences available for some of the offences listed above. The main defence for our purposes is the defence of having made an ‘authorised disclosure’ before any offence is committed.
10.2 If you make a disclosure to MLRO then that disclosure will be sufficient for you to rely on this defence, provided you disclose before any offence has been committed. This is why it is so important that you read this policy carefully, comply with its requirements and act quickly.
10.3 The MLRO will then decide whether to report the suspicion to the NCA. Where a suspicion is reported, if the MLRO does not receive a ‘refusal to proceed’ from the NCA within a seven-day period then you can proceed with the transaction. Where a ‘refusal to proceed’ is received there is a further period of 31 days for the NCA to follow up their refusal with further instructions. If no further information is received within 31 days, you can proceed with the transaction.
10.4 Note that if the MLRO does report any suspicions to the NCA you must discuss with the MLRO what information you should give to the proposed recoverable grant/loan recipient, so that you ensure you do not commit the offence of tipping off.
10.5 A person may also not be guilty of an offence if that person took all reasonable steps and exercised all due diligence to avoid committing the offence.
10.6 See PART F for reporting requirements.
11. SANCTION LISTS
11.1 There is a separate but related sanctions regime that imposes restrictions on our ability to do business with those persons and entities on OFAC, HMT, PEP, UN and EU sanctions list.
11.2 EU financial sanctions (including where they implement UN sanctions) apply within the territory of the EU and to all EU persons, wherever they are in the world. UK financial sanctions apply within the territory of the UK and to all UK persons, wherever they are in the world.
11.3 The company has developed a policy to check all transactions to confirm that no transaction involves any individual or company on the above Consolidated Financial Sanctions Lists. A sanctions search is part of our Knowing Your Customer requirements.
11.4 Hirett’s software check for all sanctions lists as part of CDD procedures.
11.5 These automated checks are made on both senders and receivers also they are part of on-going monitoring for Sender, Receiver, Staff Members and Agents.
11.6 If there is any potential match with any sanction’s lists (OFAC, HMT, PEP, UN and EU) this icon displays next to the name of person.
11.7 As a standard transaction process every transaction is checked automatically (regardless of a customer make any number of transactions per day) and if there is any Sanctions list match alert MLRO will do further checks on that transaction and advice actions accordingly.
11.8 All alerts on transactions are stored automatically.
12. DATA PROTECTION
12.1 The data protection legislation, i.e. The data protection act 2018 and the general data protection regulation (GDPR) governs the processing of information relating to individuals, including obtaining, holding, use or disclosure of information.
12.2 Personal data obtained by a business under the regulations may only be processed for the prevention of money laundering and terrorist financing unless use of the data is allowed by other legislation or after obtaining the consent of the data subject.
12.3 Hirett has a Data Protection policy which covers that personal data will only be used for the purposes of preventing money laundering and terrorist financing and provide them with the information as required under article 13 of the GDPR.
PART C. ANTI-MONEY LAUNDERING PROCEDURES – WHAT YOU NEED TO DO
13. COMPLIANCE MANAGEMENT
13.1 Hirett will carry out regular assessments of the adequacy of systems and controls to ensure that the money laundering and terrorist financing risks are managed effectively and are compliant with the Money Laundering Regulations.
13.2 It is also necessary to ensure that appropriate monitoring processes and procedures are established and maintained to regularly review and test the effectiveness of business policies and procedures.
13.3 It is the duty of MLRO to test the effectiveness of the checks they make and also the areas and indicators of risk that they have identified. A review should include consideration of the following areas:
• Are there any areas of weakness in the business where appropriate risk-sensitive checks are perhaps not being carried out in accordance with the Money Laundering Regulations / Counter-Terrorism Act requirements and the business’s policies and procedures?
• Are correct records kept in respect of evidence of ID taken and other customer due diligence checks?
• Are there any new products, services or procedures that require risk assessment, appropriate due diligence checks and internal controls putting in place? Further information on the monitoring and review of risk policy, programs and procedures can be found in this guidance.
14. MONEY LAUNDERING GUIDANCE
14.1 Hirett has drafted general guidance on The Payment Services Regulations 2019 – (“AML Guidance”) to be implemented by any staff and Agents providing Money Transfer / Money Exchange services in the United Kingdom.
14.2 In principle, AML legislation and regulations apply to individuals and institutions based in UK. UK Anti money laundering laws are applicable to British Citizens and non-citizens even if the predicate offence has been committed abroad, as long as it constitutes an offence in accordance with the laws of the foreign country and provided that the laundering act was committed within United Kingdom. Moreover, Individuals may be prosecuted for laundering acts committed in a foreign country, provided that the dual criminality requirement is fulfilled.
14.3 The purpose of the AML Guidance is:
1. To identify the legal requirements and duties to be implemented and observed by staff and Agents in UK. Each Agent must review and, where appropriate, adapt their written AML procedures to this AML Guidance. They should also inform Hirett MLRO that such adaptation has been affected.
2. To provide a single and coordinated communication and reporting system with Hirett in order to fulfil anti-money laundering duties in the UK. In this regard:
a) Hirett will designate an individual representative before the HMRC, who will act as the Hirett’s Money Laundering Reporting Officer (“MLRO”). Hirett’s MLRO will be responsible for complying with communication and reporting duties to the NCA under AML framework.
b) A centralized communication system will be established between Hirett’s MLRO and each Agent doing Money Transfer / Money Exchange business in UK for the ease of reporting obligation.
15. RISK BASED APPROACH
15.1 A risk-based approach is where you assess the risks that the business may be used for money laundering or terrorist financing and put in place appropriate measures to manage and reduce those risks. An effective risk-based approach will identify the highest risks of money laundering and terrorist financing that your business faces and put in place measures to manage these risks.
15.2 Several features of the money service business sector make it attractive to criminals, such as its worldwide reach (in the case of money remitters), the ease of making cash transactions, the one-off nature of many transactions and the speed, simplicity and certainty of transactions.
15.3 A risk-based approach should balance the costs to business and customers with a realistic assessment of the risk that business may be exploited for the purpose of money laundering and terrorist financing. It allows you to use your informed judgement to focus your efforts on the highest-risk areas and reduce unnecessary burdens.
15.4 Staff and Agents doing Money Transfer / Money Exchange business in UK should carry out an analysis of the risk exposure of money laundering in UK.
15.5 Adopting a risk-based approach implies the adoption of a risk-management process for dealing with money laundering and terrorist financing. This process encompasses:
a) recognising the existence of the risks
b) undertaking an assessment of the risks
c) developing control strategies to mitigate and monitor the identified risks.
15.6 Our strategies to manage and mitigate identified money laundering and terrorist financing risks are typically aimed at preventing the activity from occurring through a mixture of:
d) prevention, through the provision of guidance, advice and information
e) detection, through monitoring and assessment
f) deterrence, through investigation and enforcement.
HOW TO COMPLY WITH THE DUTY
15.7 Staff and Agents should draft a report analysing the risk, bearing in mind the type of customer, the type of service, the distribution channel or the amount.
15.8 Such analysis shall support the AML procedures, as defined in its written AML policies, to comply with the regulations and shall be revised on an annual basis or in any event that may cause a change of risk.
16. AML PROCEDURES
16.1 It is essential AML procedures are carried out as soon as business relationship is being established with the new customer.
16.2 ‘Know Your Customer’ checks are required to ensure that the Hirett is dealing with bona fide individuals and organisations and help identify suspicious behaviour or practices.
16.3 KYC must be included within all services so that these checks are completed prior to any due diligence decisions and business relationship being established.
16.4 The three key areas of responsibility for employees engaged in activities covered by this policy are:
• Customer Due Diligence and Know Your Customer
• Recognising and reporting knowledge or suspicion
• Maintaining records
16.5 As part of the checks you undertake to comply with CDD and KYC, you will need to assess the risks of establishing a relationship with a customer and maintaining an ongoing relationship. These considerations feed into the CDD/KYC process outlined below.
17. DUTY TO HAVE IN PLACE WRITTEN MONEY LAUNDERING POLICIES
17.1 Staff and Agents doing Money Transfer / Money Exchange business in the United Kingdom must have copy of Hirett AML policy document guiding about companies procedures about customer due diligence, reporting, record keeping, internal control, risk assessment, risk management, compliance management and communication in order to forestall and prevent operations related to money laundering or financing of terrorism through our business.
17.2 Agents doing Money Transfer / Money Exchange business with other principles and have more than one AML policy documents in place, they must;
a) endorse to Hiretts AML policy document
b) they can’t work on Hirett system without following Hirett AML policy and procedures
17.3 Also, if an agent has its own AML policy that should be in line with Hiretts AML policy and procedures for them to use Hirett systems
PART D. CUSTOMER DUE DILIGENCE AND KNOW YOUR CUSTOMER (KYC)
18. WHAT ARE CDD AND KYC?
18.1 Customer due diligence (CDD) means taking steps to identify your customers (KYC) and checking they are who they say they are.
18.2 The best way to do this is to ask for a government issued document like a passport, along with utility bills, bank statements and other official documents. Other sources of customer information include the electoral register and information held by credit reference agencies such as Experian and Equifax.
18.3 You also need to identify the ‘beneficial owner’ in certain situations. This may be because someone else is acting on behalf of another person in a particular transaction, or it may be because you need to establish the ownership structure of a company, partnership or trust.
18.4 As a general rule, the beneficial owner is the person who’s behind the customer and who owns or controls the customer, or it’s the person on whose behalf a transaction or activity is carried out.
18.5 If you have doubts about a customer’s identity, you must stop dealing with them until you’re sure.
18.6 Customer Due Diligence (CDD) – or Know Your Customer (KYC) – is a keystone in the fight against money laundering, serving to ensure our dealings are with bona fide individuals and organisations, and assisting in the identification of suspicious behaviour.
18.7 The ‘customer’ is the person or entity with whom we form a business relationship when undertaking regulated business, ie. Money Transfer or Currency Exchange. What is important is that we understand who we are dealing with and the structure of any corporate entity involved, so you must ensure that you have a fundamental understanding of the structure, management and control of the customer.
18.8 What Customer due diligence means?
• identifying all customers and verifying their identity (see Appendix 1)
• identifying all beneficial owners, where applicable, and taking reasonable measures to verify their identity to satisfy yourself that you know who they are
• obtaining information on the purpose and intended nature of the business relationship
• conducting ongoing monitoring of the business relationship, to ensure transactions are consistent with what the business knows about the customer, and the risk assessment
• retain records of these checks and update them when there are changes
• check the source of funds where you are receiving funds
• identify each Ultimate Beneficial Owner (UBO) of the customer. The UBO is a concept defined in the MLR as any individual who owns or controls 25 per cent or more of a customer.
18.9 Obtaining the KYC information is only the first step to understanding with whom we are dealing. Hirett system is designed in a way that it continuously reviews the customers data with Risk Based approach in mind and when its necessary system will automatically request additional information on that customer account. This is to enable you to know enough about the customer and it is reasonably satisfied that they are bona fide and do not pose a significant money laundering risk. You should therefore apply this policy with this objective in mind.
18.10 The CDD checks are part of Hirett’s ongoing monitoring system to ensure that the transactions are consistent with the customer’s business and risk profile and that data, information and documentation is kept up to date for the purpose of applying CDD measures. The procedure shall be more stringent in case of new customers.
WHEN MUST IT BE DONE?
18.11 complete customer due diligence on all customers and beneficial owners before entering into a business relationship or undertaking an occasional transaction that requires due diligence (at £0 transaction)
18.12 An occasional transaction that amounts to HMRC threshold (see Appendix 2) or more, whether the transaction is executed in a single operation or in several operations which appear to be linked.
18.13 complete customer due diligence when you suspect money laundering, or have doubts about the documents or information previously collected for customer due diligence
18.14 have adapted procedures to identify those who cannot produce standard documents, for example, a person not able to manage their own affairs identify and verify a person acting on behalf of a customer and verify that they have authority to act
18.15 apply enhanced due diligence to take account of the greater potential for money laundering in higher risk cases, including in respect of politically exposed persons and persons established in high risk third countries.
18.16 apply customer due diligence when you become aware that the circumstances of an existing customer have changed. This may require you to review the extent of due diligence undertaken, for example applying enhanced due diligence if the customer now represents a higher risk
18.17 not deal with certain persons or entities if you cannot do customer due diligence and consider making a suspicious activity report
18.18 Hirett automatically keep copies of customer due diligence and supporting records in our cloud-based software, please make sure this information up to date
18.19 understanding the legal and beneficial ownership or control structure of a customer when the customer is one of the following:
• legal person
• trust
• company
• foundation or
• similar legal arrangement
18.20 The MLR requires that evidence of identity be obtained whenever:
• a new business relationship is established (ie. Open new account for an individual or entity we have not previously transacted with)
• you have a suspicion of money laundering or terrorist financing
• you have doubts about the validity or adequacy of the documents obtained while conducting the identification exercise
• where the risk profile of the recipient changes over the course of the transaction or during the period of an ongoing relationship, eg. a company structure changes, a new beneficial owner or a Politically Exposed Person (PEP).
19. LINKED TRANSACTIONS
19.1 Linked transactions are individual transactions of less than HMRC suggested threshold (see Appendix 2) that have been deliberately broken down into separate, smaller transactions to avoid customer due diligence checks. Hirett software automatically detects all linked transactions associated with customer.
19.2 Once linked transaction has been identified, you need to decide if it has been deliberately split. Some issues to consider are when:
• a number of payments have been made by the same customer in a short period of time
• it’s possible that a number of customers have carried out transactions on behalf of the same person
• a number of customers have sent money transfers to the same person
1..1.2 Hirett’s system automatically accumulates all linked transactions to determine if the threshold (See Appendix 2) is met and EDD is required.
1..1.3 Hirett’s system also flag customer if they try to register at multiple Hirett locations to avoid CDD.
1..1.4 Hirett’s software automatically accumulates transactions from all locations for same customer and flag customer for further EDD / Source of Funds information request.
20. CUSTOMER DUE DILIGENCE – PRIVATE CLIENT
20.1 If the customer returns to process a transaction which meets threshold (See Appendix 2) either as a one off or series of linked transactions within three months, Hirett would perform Enhanced due diligence.
20.2 Each customer is also required to confirm whether or not they are processing transactions for third party / PEP. If the sending customer confirms that they are sending money on behalf of Third Party / PEP then this transaction must be declined.
21. CONDUCTING CUSTOMER DUE DILIGENCE AND ENHANCED DUE DILIGENCE
21.1 It is a legal requirement that all the Hirett agents / staff offering the money service business should inform the money laundering officer (MLRO) whenever any suspicious transaction takes place. Accordingly, to be able to identify a suspicious transaction, it is important that each with responsibility for handling transaction should get to know their customers.
21.2 Hirett has remittance software for money transfer customers so that the true identity of all those people who send money through Hirett’s system can be recorded.
21.3 As a matter of policy Hirett staff / agents will be abide by the following KYC policy in their daily operation.
21.4 For larger transaction documentary evidence would be required for source of funds (see Appendix 3) that is if a customer sends funds equal to any threshold limit (see Appendix 2) and declares the source of funds is a bank loan, either a loan agreement or any correspondence from the bank may be required and bank statement showing the balance in the account in other case they require to produce payslips or any other source of funds reflecting in bank statement.
22. WHAT IS ENHANCED DUE DILIGENCE (EDD)?
22.1 If the business needs to establish more information about the customer and /or for the transaction. This means that the customer should be asked to provide:
1. More ID information (i.e. Further proofs of ID/proof of address)
2. More information about the source of funds for the transaction (including possibly a written proof of source of funds)
3. More information on the purpose of the transaction
4. In the event that the customer cannot provide more information, or provides information which gives rise to suspicion, then the MLRO will freeze the transaction and will make a report to the NCA.
IDENTIFICATION – WHAT CHECKS YOU SHOULD MAKE OF THE ID EVIDENCE GIVEN:
1. Check any photographs for true likeness;
2. Check the date of birth compared to the customer’s age;
3. Compare spelling of names and addresses on different identification documents;
4. Compare the signatures with the signature in the identification evidence.
5. Check for the authenticity of the ID provided as there are lots of counterfeit Passport, Driving Licenses and Asylum Seeker’s documents.
23. LINKED TRANSACTIONS
It is company policy that transactions are ‘linked’ when the following criteria apply:
23.1 Linked transactions may be a series of transactions by a legitimate customer, or they may be transactions that appear to be independent but are in fact split into two or more transactions to avoid detection. This typically happens when a customer tries to avoid anti-money laundering controls by splitting transactions into several smaller amounts, below the level at which you check ID or enquire about the source of funds. Hirett have a system to detect linked
23.2
23.3 transactions, and to undertake enhanced due diligence on them, and report any suspicious activity when they’re detected.
23.4 There is no specific time period over which transactions may be linked, after which enhanced due diligence is not necessary. The period of time depends on the customers, service and destination countries.
HMRC recommends that businesses consider checking for linked transactions over a minimum rolling 90-day period.
23.5 Hirett operates through agents and its own branches, our system is designed to identify linked transactions that are conducted through all of our locations.
23.6 The same sending customer has sent €7,500 (or local equivalent) or more in the last three months to the same receiving customer in a number of individual transactions (or €7,500 within one month).
23.7 Three sending customers or more are sending to the same receiving customer (or receiving address or receiving telephone number) AND the receiving customer or bank account has received more than €7,500 (or local equivalent) in last 3 three months (or €7,500 within one month)
23.8 A sending customer is sending funds on behalf of one or several people
23.9 In the event that ‘linked’ transactions are identified, they should be notified to the MLRO who will determine whether or not there are any suspicious circumstances which mean the transaction should be reported to NCA.
24. CRITERIA FOR DETECTING LINKED TRANSACTIONS
Hirett has software in place that detects any linked transaction
24.1 If a customer is sending money over the threshold limit (See Appendix 2) to a single receiver or more than 1 receiver with in time period of 3 months
24.2 If one receiver is receiving money over (See Appendix 2) or more from single sender or more than 1 sender within in 3 months of period
24.3 If the sender is sending transactions from more than 1 location of Hirett
lick edit button to change this text.
25. SOURCE OF FUNDS – WHEN TO VERIFY
25.1 Any sending customer will be requested to provide written proof of source of funds (See Appendix. 4) for any one off or linked transaction of threshold (See Appendix 2) or more. Acceptable proofs will include:
• Source of funds declaration
• Mini statement-attested by bank
• Bank statement less than three months old
• Letter of secured or unsecured loan
• ATM receipt/Withdrawal receipts with bankcard
• Wage slip for last 3 Months
• Or other acceptable document (i.e. source of funds declaration)
• Sale of assets/Property Invoice
25.2 In the event that the customer is unable to provide any of this information, the transaction must be refused.
25.3 If any customer does cumulative transactions which total the threshold limit (See Appendix 2) or more than €15,000 (or local equivalent) as described by HMRC threshold limit, in 90 days period, then customer will be asked to provide proof of address plus documentation of source of funds (See Appendix. 4) again.
25.4 A failure to do so will be regarded as suspicious and a report should be made to NCA.
25.5 Source of funds information is automatically asked by System when threshold is met, please see appendix 4.
CHANGES AND MODIFICATIONS TO CUSTOMER’S DETAILS
25.6 All customers should be made aware that information is held for 5 years – random checks may be made on information supplied and if any details are incorrect, customers will be suspended from the system until the customer supplies the updated personal information.
25.7 Agents / Staff should particularly take care to make sure that customer ID information previously supplied is still valid (and that ID documents have not expired).
25.8 Any customer address information provided should be re-verified at least every twelve months
26. NON-COMPLIANCE WITH CUSTOMER DUE DILIGENCE MEASURES
26.1 Money Laundering Regulations requires that where a business is unable to comply with the required customer due diligence measures in relation to a customer, then the business must:
• Not establish a business relationship
• Not carry out a transaction with or for the customer
• Not carry out an occasional transaction with the customer
• Terminate any existing business relationship with the customer
• Consider making a report to NCA.
• If the problem is caused by the customer not having the ‘right’ documents or information, perhaps because the person is financially excluded, consideration should be given to whether there are any other ways of being reasonably satisfied as to the customer’s identity.
• If there are no grounds for making a report to NCA, you should return the funds, ideally in a way that minimizes the risk of the returned funds being effectively laundered in the process.
• If you decide that the circumstances give reasonable grounds for knowledge or suspicion of money laundering or terrorist financing, you must retain the funds until consent from NCA has been obtained to return them.
27. WHEN TO ACCEPT OR DECLINE A TRANSACTION
27.1 If a potential or existing customer either refuses to provide the information described above when requested, or appears to have intentionally provided misleading information, the Company will not conduct Any / further money service transactions with that person.
27.2 Transaction must be declined if the customer is unable to provide the required ID and proof of address documents when requested to support the transaction, plus any other documents which may be necessary to demonstrate source of funds.
27.3 It is at the discretion of each employee to decide whether to accept or decline a transaction.
27.4 Each employee and agent should have a clear understanding of this policy, the MLRO must keep an eye on the transactions which are being processed and make sure that any transactions, which may be suspicious, are reported as soon as possible.
27.5 Employee / Staff may question customers in order to clarify the nature of a transaction, but should avoid ‘tipping off’ the customer.
27.6 In either case, Compliance Officer must be notified so that he can determine whether he should report the situation to NCA.
PART E. BUSINESS RELATIONSHIPS / ACCEPTABLE CLIENTELE
28. WHAT IS A BUSINESS RELATIONSHIP?
28.1 The customer is the person or entity with whom Hirett forms a contractual relationship or provides a service to.
28.2 This is the individual or company sending money or exchanging currency made out to them. For example, a business relationship for Hirett exists where:
• A unique customer number is allocated and a customer registration form is completed.
• Customers are able to deposit cash into the company bank account.
• Customers can make transactions by telephone or over the internet.
• Giving preferential rates to repeat customers.
28.3 Hirett also accepts business from other third-party money service businesses (Agents), it is either as a currency wholesaler or as a money transmitter acting as an intermediary in a money remittance chain, hence our agents are our customers as well, and the owners or controllers of the agent’s business are beneficial owners. Hirett applies customer due diligence to each of its agents along with other fit and proper requirements.
29. ONGOING MONITORING OF A BUSINESS RELATIONSHIP
29.1 Hirett continuously monitors its business relationship after they are established through an automated system. This means we monitor transactions, and where necessary the source of funds, to ensure they are consistent with the KYC of the customer and the customer’s business and the risk assessment. As part of your ongoing monitoring the following requirements are reviewed:
• the risk assessment for the customer
• beneficial ownership of the customers who are a corporate structure
• when there is a difference in business pattern
• when the relevant business becomes aware that the circumstances of an existing customer, relevant to its risk assessment for that customer has changed.
29.2 Hirett keeps the information collected for this purpose up-to-dated. We check for any expired documents such as passport and driving licenses at every transaction and request replacements with copies of newly issued documents before processing transaction.
30. BENEFICIAL OWNERSHIP
30.1 Beneficial owners are individuals who ultimately own or control the customer, or on whose behalf a transaction or activity takes place.
30.2 For a corporate body that is not a company whose securities are listed on EEA regulated markets and certain other main markets1, a beneficial owner is any individual who:
1. owns or controls over 25% of the shares or voting rights
2. ultimately owns or controls whether directly or indirectly including bearer shares holdings or other means, more than 25% share or voting rights in the business
3. holds the right, directly or indirectly, to appoint or remove a majority of the board of directors
4. has the right to exercise, or actually exercises, significant influence or control over the corporate body exercises ultimate control over the management
5. controls the corporate body
30.3 Where the customer is a legal person, trust, company, foundation or similar, you must take reasonable measures to understand their control structure, as well as who is the beneficial owner.
| WHO | REQUIREMENTS |
| Individuals | If a customer is an individual, you must identify them as part of your customer due diligence. You should obtain a private individual’s 1 Government issued ID and residential address as a minimum.
Hirett only accepts original documents we do not accept photocopies as part of our due diligence. Required Documentation: Annex A |
| Third Party Payments | Where an individual claims to act on behalf of a customer, you must also obtain evidence that the individual has the authority to act for them, identify the individual and verify their identity. Evidence that the individual has the authority to act may be through a call to the customer with a confirmation email by return, legal documents, Companies House information showing a connection or third-party confirmation.
**We don’t deal with Third Party Payments** |
| Registered charities | For customers who are charities, you must obtain and verify identity information that is relevant to that entity. This includes:
• the full name of the company • company or other registration number • registered address and principal place of business • ownership and control structure of the entity **We don’t deal with Charities ** |
| Trusts | Where the customer is a trustee acting on behalf of a trust, you must identify and verify the identity of the trustee(s) and assess – and where appropriate obtain information on – the purpose and intended nature of the business relationship or occasional transaction. You should also identify and verify the identity of the settlor and identify/verify the identity of other beneficial owners of the trust on a risk-sensitive basis, and in accordance with your assessment of the risk associated with the customer relationship.
**We don’t deal with Trusts** |
| Corporate Clients | You should establish the names of all directors (or equivalent) and must identify the ultimate beneficial owners (the section on beneficial ownership provides information on who they are). You must look through the ownership structure of any companies or trusts to establish the ultimate beneficial owners. If you exhaust all means of identifying the beneficial owner, you must take all reasonable steps to verify the identity of the senior person. You must keep a written record of all the steps you have taken and who you have identified.
Required Documentation: Annex B **We are currently not on-boarding Corporate Clients** |
| Shell Bank | shell bank means a bank that has no physical presence in the country in which it is incorporated and licensed, and which is unaffiliated to a regulated financial group that is subject to effective consolidated supervision.
**We don’t deal with Shell Banks** |
| FATF Non-Compliant / Black Listed Jurisdictions | The FATF blacklist, now called the “Call for action” jurisdictions. There is a list of “Non-Cooperative Countries or Territories” (NCCTs). These jurisdictions have significant strategic deficiencies in their regimes to counter money laundering, terrorist financing, and financing of proliferation.
**We don’t deal with countries listed in NCCTs** |
| PEP | A politically exposed person (PEP) is an individual with a high-profile political role, or who has been entrusted with a prominent public function.
Any relative or close associate of PEP also considered high risk. More details about PEP’s is provided in sections below. **We don’t deal with PEPs** |
31. POLITICALLY EXPOSED PERSONS (PEPs)
31.1 Politically exposed persons are persons that are entrusted with prominent public functions, whether in the UK or abroad. This is because international standards issued by the Financial Action Taskforce (FATF) recognise that a PEP may be in a position to abuse their public office for private gain and a PEP may use the financial system to launder the proceeds of this abuse of office.
31.2 The definition does not include:
- middle ranking or more junior officials
- persons who were not a politically exposed person under the 2007 regulations where they ceased to hold a prominent public function prior to 26 June 2017, such as former MPs or UK Ambassadors
31.3 Politically exposed persons include:
- heads of state, heads of government, ministers and deputy or assistant ministers
- members of parliament or similar legislative bodies
- includes regional governments in federalised systems and devolved administrations, including the Scottish Executive and Welsh Assembly, where such bodies have some form of executive decision-making powers. does not include local government in the UK but it may, where higher risks are assessed, be appropriate to do so in other countries.
31.4 Members of the governing bodies of political parties
-
- member of a governing body will generally only apply to the national governing
- bodies where a member has significant executive power (e.g. over the selection
- of candidates or distribution of significant party funds).
- political parties who have some representation in a national or supranational
- Parliament or similar legislative body.
31.5 Members of supreme courts, of constitutional courts or of any judicial body the decisions of which are not subject to further appeal except in exceptional circumstances; in the UK this includes judges of the Supreme Court but does not include any other member of the judiciary
31.6 Members of courts of auditors or boards of central banks
31.7 Ambassadors, and high-ranking officers in the armed forces
-
- where persons holding these offices on behalf of the UK government are at Permanent Secretary or Deputy Permanent Secretary level, or hold the equivalent military rank e.g. Vice Admiral, Lieutenant General or Air Marshal
31.8 Members of the administrative, management or supervisory bodies of state-owned enterprises
-
- this only applies to for profit enterprises where the state has ownership of greater than 50% or where information reasonably available points to the state having control over the activities of such enterprises
31.9 Directors, deputy directors and members of the board, or equivalent of an international organisation.
-
- includes international public organisations such as the UN and NAT does not include international sporting federations.
31.10 The Regulations require that family members of PEPs must also have enhanced due diligence measures applied to them. For these purposes, the definition of “family member” includes:
-
- spouses/civil partners of PEPs;
- children of PEPs and their spouses/civil partners
- parents of PEPs
- brothers and sisters of PEPs.
31.11 Known close associates are persons who have:
-
- joint legal ownership, with a politically exposed person, of a legal entity or arrangement
- any other close business relationship with a politically exposed person
- sole beneficial ownership of a legal entity or arrangement set up for the benefit of a politically exposed person.
31.12 It is a matter of company policy that all customers will be required to indicate whether they or any member of their family has previously worked in a non EU country at any time in the preceding 12 months. In case the answer is yes, the cashier must make enquiries to establish whether the customer may meet the criteria for being ‘politically exposed’.
31.13 Hirett system automatically check each transaction against known PEPs sanction list to avoid human error.
32. IN CASES WHERE PEP IS IDENTIFIED:
32.1 It is a policy of Hirett not to deal with PEP’s
32.2 It is a part of customer on-boarding procedure to ask question about PEP and association with PEPs in any capacity (i.e: as a PEP relative or PEP associate).
32.3 If during the transaction monitoring (which is done on every transaction made through Express System) any PEP flags up on any sender / receiver, MLRO will make further checks on that flag and take additional steps which could be from declining transaction to terminating customer’s account in some situations.
PART F. SERVICES AND BUSINESS MODEL
Hirett offers following regulated services:
• Money Transfer
• Currency Exchange
33. PRINCIPAL–AGENT BUSINESS MODEL
33.1 Hirett offer its services under principal – agent model, this includes;
1. appointing an agent or agents to act on behalf of a money service business (the principal) in the provision of their services. For example, this may be to:
a) accept money transmission instructions from customers
b) accept cheques for encashment
c) undertake currency exchange
2. appointing agents, to distribute certain products, for example supply and operate automated terminals or services such as bill payment terminals.
3. Acting as a principal in this context means that Hirett is the party that contracts with a customer through its agent and owns and is responsible for the transaction.
4. In a principal-agent relationship, the principal is the person or entity who gives authority to an agent to act on the principal’s behalf. However, the responsibilities of the principal do not absolve an agent from its legal obligations to comply with the Regulations and the Proceeds of Crime Act.
5. An agent is a separate person or entity, who are appointed to act on behalf of the principal in the provision of their services. This arrangement may be directly between agent and principal or may be a between an agent of the original principal and a further agent.
34. MONEY TRANSFER
EU PAYMENTS REGULATION:
34.1 Implemented in the EU as the Transfer of Funds (information on the payer) Regulations 2019) requires Money Transfer Businesses to obtain customer’s information when undertaking the transfer of customer’s funds into and out of the EU. This means:
MONEY TRANSFER TRANSACTION PROCESS
STEP 1 – COLLECT AND RECORD CUSTOMER INFORMATION
34.2 You must collect and retain 1 x Government issued ID of the sending customer’s name and address.
34.3 The information collected is known as Complete Information on the Payer (CIP).
34.4 Prior to engaging in any money service activity which potentially may involve money laundering, you should collect the following information for all customers where necessary: the name; an address, (which will be a residential or business street address for an individual), one or more of the following: Valid passport number and country of issuance, valid Driving license.
34.5 You should refuse any money service transaction in the event that a customer has required providing identification documents and cannot prove his/her identity to the satisfaction of the MLRO.
STEP 2 – VERIFY THE CUSTOMER INFORMATION PROVIDED
34.6 Hirett’s system verifies each and every transaction through automated system in place.
34.7 Based on the risk, and to the extent reasonable and practicable, staff and agents must ensure that you have a reasonable belief that you know the true identity of customers by using risk-based procedures to verify and document the accuracy of the information you get about the customers.
34.8 In verifying customer identity, you must analyse any logical inconsistencies in the information you obtain.
34.9 You must verify customer identity through documentary evidence, non-documentary evidence, or both.
34.10 You must use original documents only to verify customer identity. In light of the increased instances of identity fraud, you should supplement the use of documentary evidence by using the non-documentary means described below whenever possible.
34.11 You may also use such non-documentary means, after using documentary evidence, if you are still uncertain about whether you know the true identity of the customer.
34.12 In analysing the verification information, you must consider whether there is a logical consistency among the identifying information provided, such as the customer’s name, street address, post code, telephone number (if provided), date of birth, Government Issued ID.
34.13 Appropriate documents for verifying the identity of customers include, but are not limited to, (See Appendix 1)
34.14 We understand that you are not required to take steps to determine whether the document that the customer has provided to you for identity verification has been validly issued and that you may rely on a government-issued identification as verification of a customer’s identity.
34.15 However, if you note that the document shows some obvious form of fraud, we must consider that factor in determining whether we can form a reasonable belief that we know the customer’s true identity.
34.16 You may also use any or all of following non-documentary methods of verifying identity:
• Contacting a customer;
• Independently verifying the customer’s identity through the comparison of information provided by the customer with information obtained from a consumer reporting agency, public database, employer or other source;
• Checking references with financial institutions;
STEP 3 – LACK OF VERIFICATION
34.17 When we cannot form a reasonable belief that we know the true identity of a customer, we will do the following:
• Do not perform any money service transaction;
• Impose terms under which a customer may conduct transactions while you attempt to verify the customer’s identity;
• File an internal SAR to MLRO who will further investigate the customer.
STEP 4 – SEND THE INFORMATION WHICH HAS BEEN GATHERED TO THE PAYOUT SERVICE PROVIDER IN THE PAYOUT COUNTRY
34.18 If the transfer of funds is to a destination outside the EU, complete payer information (full CIP) must accompany the transfer.
34.19 Full CIP may be defined as one of the following combinations of information: Customer name plus address plus transaction number, Customer name plus date and Place of birth plus transaction number Customer name plus customer ID number/Passport plus transaction number.
34.20 The key requirement is that enough information should be sent to the PSP (Payment service Provider) of the payee so that the transaction is traceable back to the originating customer.
34.21 Hirett system automatically send above information to the payout banks.
TRANSACTION PROCESSING
34.22 All money transfer transactions are in cash, by internet, by apps or from the customer’s bank account to the Company bank account.
34.23 Non face to face transactions over the telephone are permissible for already registered customers but customer will be required to quote their customer ID and should also be asked to answer security questions.
34.24 When a retail customer makes an approach in person to the company with a request to transfer funds, he or she is required to complete KYC on that customer which requires certain information (see below) about the sending customer and the beneficiary. This information is recorded by the cashier in the Company’s money transfer software.
34.25 Each customer is assigned a customer ID number when they process the first transaction and each transaction is given a unique transaction number. Each sending customer is also given the PIN number on receipt. They need to pass the PIN number to the beneficiary to allow them to pick up the funds in the receiving country.
34.26 Upon completion of the transaction, the customer is offered a receipt which records all the details of the transaction. The company will keep complete records for each transaction showing the following:
1. Unique transaction number
2. Sending customer ID number (generated by the company)
3. Sending customer name
4. Sending customer address (including full postcode)
5. Sending customer telephone number
6. Transaction amount
7. Exchange rate
8. Fee charged
9. Pay out bank account
10. Pay out location
11. Receiving customer name
12. Receiving customer address
13. Receiving customer telephone
34.27 All customers need to be made aware to check payment receipt for any error of details so this could be amended urgently also they can make a complaint to the business in the first instance if they are not happy with any aspect of the way the transaction has been processed.
34.28 Any complaint must be processed in line with the complaints handling process established by the business (see complaints handling policy document).
35. CURRENCY EXCHANGE
35.1 Currency Exchange businesses are exploited to change small denomination notes into large denominations in another currency to enable easier and cheaper handling of large quantities of illegal cash – once the money has been exchanged, it’s difficult to trace its origin.
35.2 Criminals try to identify any weakness in a currency exchange’s anti-money laundering controls in order to exploit them.
35.3 Staff and Agents must keep an eye for the following are risk indications in relation to new / existing customers of currency exchange business:
i. they request high denomination notes such as €100, €200, and €500 notes or $100 US notes
ii. the customer’s willing to accept poor rates of exchange
iii. the customer’s unable to provide satisfactory evidence of the source of the funds
iv. unusual source of funds
v. non face-to-face customers
vi. the customer is buying currency that doesn’t fit with what the business knows about their travel destination
vii. the customer wishes to exchange large volumes of low denomination notes
viii. border transaction
35.4 The sale of high value notes, in any currency, entails a significant money laundering risk. All the major UK banks and financial institutions have agreed not to sell €500. You should regard any request to buy or sell €500 notes as potentially suspicious.
35.5 You should refuse to sell €500 notes and submit a suspicious activity report.
35.6 Requests for high denomination notes by a customer should be treated as high-risk and you should do enhanced due diligence checks and submit a suspicious activity report if appropriate.
PART G. RISK ASSESSMENT
36. RISK BASED APPROACH
36.1 A risk-based approach starts with the identification and assessment of the risk that has to be managed.
36.2 A risk-based approach requires a number of steps to be taken to determine the most cost-effective and proportionate way to manage and mitigate the money laundering and terrorist financing risks faced by the business. The steps are to:
- Identify the money laundering and terrorist financing risks that are relevant to the business
- Assess the risks presented by the particular
- Customers – types and behavior
- Products and services
- Delivery channels, for example, cash over the counter, electronic, wire transfer or cheque
- Geographical areas of operation, for example, location of business premises, source or destination of customers’ funds
- Design and implement controls to manage and mitigate these assessed risks
- Monitor and improve the effective operation of these controls and Record appropriately what has been done, and why.
36.3 A risk assessment will often result in a stylized categorization of risk, for example,
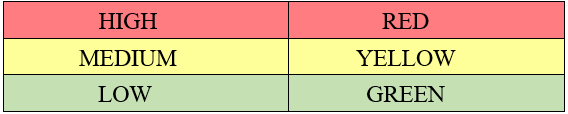
36.4 Criteria will be attached to each category to assist in allocating customers and products to risk categories, in order to determine the level of identification, verification, additional customer information and ongoing monitoring, in a way that minimizes complexity.
36.5 Hirett assess the risk by considering the following questions;
WHAT RISK IS POSED BY THE CUSTOMER?
• New customers carrying out large one-off transactions
• Customers engaged in a business which involves significant amounts of cash
• Complex business ownership structures with the potential to conceal underlying beneficiaries
• A customer or group of customers making frequent transactions to the same individual/group of individuals
• An individual (or an immediate relative) holding a public position and/or situated in a location which carries a risk of exposure to the possibility of corruption
• Customers based in, or conducting business in or through, a high-risk jurisdiction, or a jurisdiction with known higher levels of corruption, organized crime or drug production/distribution
• There has been a significant or unexpected improvement in the customer’s financial position
• The transaction is different from the normal business of the customer, that do not make commercial sense or involved in transactions where the source of funds is unusual or unknown;
• Customers that are carrying out transactions, or business relationships with countries where financial action task force has highlighted deficiencies in systems to prevent money laundering and terrorist financing.
• the pattern has changed since the business relationship was established
• the size and frequency of the transaction is different from the customer’s normal pattern
• Customer’s name flagged in Sanctions List
IS A RISK POSED BY A CUSTOMER’S BEHAVIOR?
• An unwillingness to produce evidence of ID or the production of unsatisfactory evidence of ID
• Where the customer is, or appears to be, acting on behalf of another person, an unwillingness to give the name/s of the person/s they represent
• A willingness to bear very high or uncommercial penalties or charges
• Situations where the source of funds cannot be easily verified.
HOW DOES THE WAY THE CUSTOMER COMES TO THE BUSINESS AFFECT THE RISK?
• Occasional or one-off transactions as opposed to business relationships
• Introduced business, depending on the effectiveness of the due diligence carried out by the introducer
• Non face-to-face transactions.
WHAT RISK IS POSED BY THE PRODUCTS/SERVICES THE CUSTOMER IS USING
• Do the product and services facilitate sanctions customers type? (PEP, Third Party, etc.)
• Is there a risk of inappropriate assets being placed with, or moving through the business?
37. RISK IDENTIFICATION AND RANKINGS
37.1 The risks inherent in the industry and faced by our business and the policies and procedures in place to;
• A high volume of cash transactions creates an opportunity for placement of criminal cash, including through “smurfing”. It is the issue of transactions structured to avoid certain record keeping and reporting requirements mandated by law. In this regards we have certain polices such as KYC policy. Over and above this our money transfer software
has such features to stop transaction which are suspicious in nature and show signs of‘ ‘smurfing’.
• Remittance of funds to countries with high levels of organised crime or drug production / distribution.
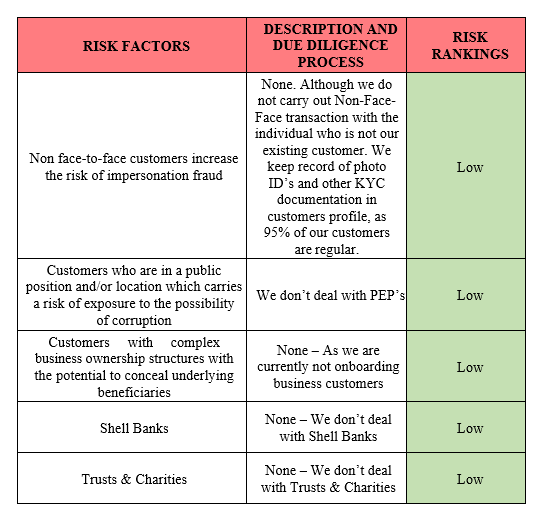
37.2 We send money to higher risk countries and we always check as best we can with the remitter to understand the purpose the money is being sent.
37.3 We manage our AML Compliance on transactions through our head-office which actually being operated by Hirett staff.
38. RISK FACTORS, RESPONSE AND RANKINGS
38.1 Risk should be assessed in relation to:
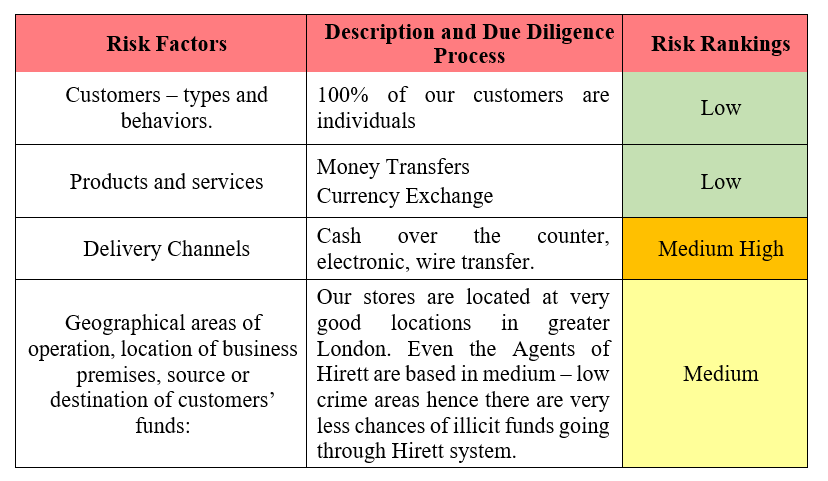
38.2 Risk factors that are relevant to the business and document the actions that will be taken to mitigate these risks as they arise, i.e. the types of customer due diligence and on-going monitoring measures that will be applied, or the management controls in place within the business.
38.3 The table below includes examples of the types of risk factors that may be relevant.
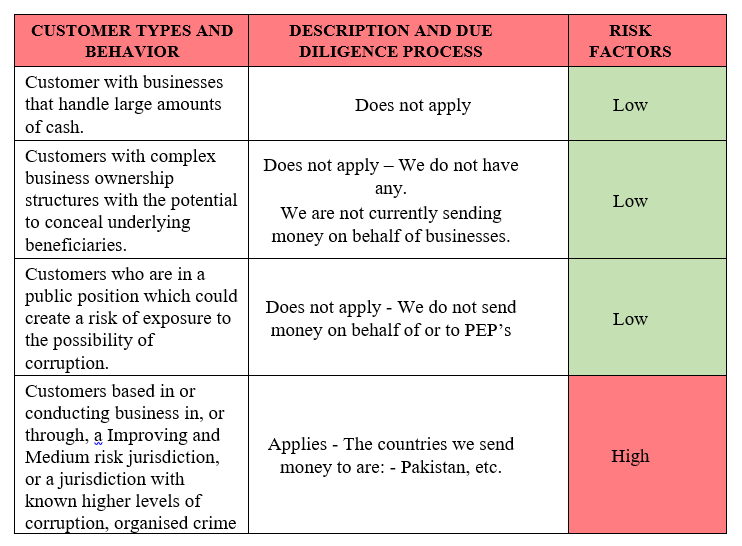
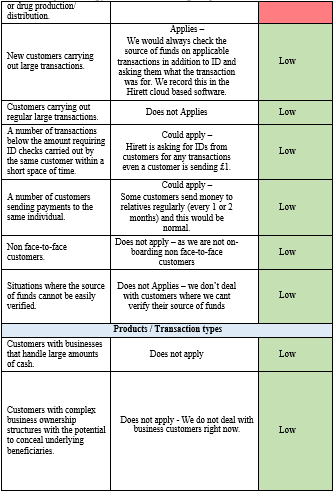
38.4 There is a separate Risk Assessment document detailing assessment of all business areas and product and services. This document should be seen with this AML policy.
39. RISK MONITORING
39.1 Risk assessment must also include the review and monitoring of the money laundering and terrorist financing risks to the business. The risk-based approach by the business will be informed by the monitoring of patterns of business, for example:
• A sudden increase in business from an existing customer
• Uncharacteristic transactions which are not in keeping with the customer’s known activities
• Peaks of activity at particular locations or at particular times
• Unfamiliar or untypical types of customer or transaction
40. MANAGING AND MITIGATING THE RISK
40.1 Once the business has identified and assessed the risks it performs the following tasks to manage and mitigate the risk:
1. Applying customer due diligence measures to verify the identity of customers and any beneficial owners
2. Obtaining additional information on higher risk customers
3. Conducting ongoing monitoring of the transactions and activity of customers with whom there is a business relationship
4. Having systems to identify and scrutinize unusual transactions and activity to determine whether there are reasonable grounds for knowing or suspecting that money laundering or terrorist financing may be taking place.
HIRETT WILL PERFORM THE FOLLOWING RISK-BASED CONTROL:
• Introducing customer identification and verification procedures at a lower monetary level than the minimum threshold set out for occasional transactions in the Money Laundering Regulations in circumstances, where the customer or other characteristics of the transaction are in a higher risk category
• Requiring ID evidence – whether it be documentary, electronic or third-party assurance – to be of a certain standard
• Requiring additional evidence of identity in higher risk situations
• More extensive due diligence checks, for example, on source of funds, for higher risk customers
• Varying the level of monitoring of customer transactions and activities according to identified risk to identify transactions or activities that may be unusual or suspicious.
40.2 This list of suggested controls is not exhaustive. Staff and Agents must decide what checks and controls are appropriate to address the risks that they have identified within their business activities.
40.3 Identifying a customer or transaction as being of a higher risk does not automatically mean that the customer/transaction is involved with money laundering or terrorist financing. Similarly, a customer/transaction seen as low risk does not mean that the customer/transaction is not involved with money laundering or terrorist financing. Employees and Agents of the business therefore need to be vigilant, and use their experience and common sense when applying the business’s risk-based criteria and rules.
41. MONITORING AND IMPROVING THE EFFECTIVENESS OF CONTROLS
41.1 The risk-based approach that should be considered for monitoring and review include:
• procedures to identify changes in customer characteristics or behaviour
• the ways in which products and services may be used for money laundering or terrorist financing, recognizing how these ways can change, with reference to information and typologies supplied by law enforcement feedback
• the adequacy of staff training and awareness
• compliance monitoring arrangements, for example, internal audit/quality assurance processes or external reviews
• the balance between technology-based and people-based systems
• capturing appropriate management information
• upward reporting and accountability
• internal communication
• Effectiveness of the liaison with regulatory and law enforcement agencies.
PART F. SUSPICIOUS ACTIVITY REPORTS – INTERNAL COMPANY PROCESS
42. SUSPECIOUS ACTIVITY REPORT
42.1 In the situation that an employee, agent or agent employee (for this purpose, collectively, staff members) has suspicions about a customer and/or transaction, he must ensure that the company MLRO is notified about his suspicions as soon as possible.
42.2 Staff should use the internal ‘Suspicious Activity Report Form’. The SAR should contain as a minimum the following information:
• Date/time of transaction
• Amount
• Customer name/customer ID information (e.g. passport number, etc)
• Transaction number
• Reason for suspicion of transaction
42.3 Hirett has an automated e-SAR system which is part of Hirett software, all agents / staff must use e-SAR to report any suspicious transaction.
42.4 If in doubt, the staff member should call the MLRO to discuss the reasons for their suspicion – however, they should be careful not to do this whilst the customer is standing in front of them (they may ‘tip off’ the customer otherwise, see below).
42.5 In the situation where the staff member works for an agent, the report should be made in the first instance to the Agent MLRO, who must then report on to the company MLRO.
42.6 The timing for submitting the internal SAR is important. The law states that an individual working in the regulated sector (i.e. a money transfer company, currency exchange business) should make a report as soon as he or she becomes suspicious. This may mean either before the transaction takes place or immediately afterwards.
42.7 Where a staff member becomes aware that a customer wants to carry out a transaction which is suspicious and the timing for the transaction allows it, the staff member must ensure that ‘consent’ is given before processing the transaction. ‘Consent’ means that the company has sought and obtained approval from the Financial Intelligence Unit at the National Crime Agency (NCA) to process the transaction. Further information on ‘seeking consent’ is provided below.
42.8 However, staff may decide that there would be a danger that if they were to seek consent for a particular transaction (i.e. in advance of the transaction taking place) that there might be a danger that the customer would be ‘tipped off’. See below for more information on ‘tipping off’ and ‘seeking consent’.
42.9 All staff members will have fully discharged their duties, and will have the full protection of the law, once a report of their suspicions has been made to the company MLRO.
43. CUSTOMER BEHAVIOUR
43.1 A transaction is suspicious if the customer:
• Splits a single large transaction into small transactions to avoid producing ID also known as smurfing.
• Always send money under the large transaction limit
• Offers a legitimate ID which appears to have been altered
• Refuses to provide ID or proof of address
• Tries to establish conversation with the employee on other subjects to distract you
• Doesn’t show any concern about the rates or charges
• Doesn’t know how much money he is sending
• Has unusual needs or wishes in relation to the transaction
• Says he is transferring money for a third party
• Is reluctant to give the information requested for proper identification
• Provides an ID document where the photo does not match the customer’s appearance
• Appears to be unemployed, but regularly carries out large transactions
• Is a regular customer without a local address, who appears to reside locally because he or she is a repeat customer
• Offers a tip to process the transaction
• Carries out a level of transactions which are inconsistent with his background
• Is willing to pay more commission if he doesn’t have to show his passport
• Comes in with people who ‘hang around’ whilst he does the transaction
• Is inquisitive about the company secrecy policy or reporting procedures
• Asks what is the maximum amount he can send without providing ID
• Seems respectable, but carries money in a plastic bag
• The money contains large number of Scottish notes
• Carries out several transactions in a day or week
44. SEEKING ‘CONSENT’
44.1 Staff may encounter situations when processing a transaction where a request needs to be made to NCA ‘seeking consent’ to undertake acts which would be prohibited as a principal money laundering offence. The idea behind consent is that the company is seeking a permission to proceed with the transaction before the transaction is finally processed.
44.2 NCA has up to 7 days to confirm whether or not the transaction for which consent has been requested can proceed – until NCA give consent, the transaction cannot proceed – it is frozen. In these circumstances, the staff member must be very careful that they do not ‘tip off’ the customer about the reason for the delay in processing the transaction.
44.3 Where NCA gives notice that consent to a transaction is refused, a further 31 day period (the “moratorium”) commences on the day that notice is given. The 31 days include Saturdays, Sundays and public holidays. It is an offence to undertake the act during this period as the participant would not have the appropriate consent. The moratorium period enables NCA to further their investigation into the reported matter using the powers within Proceeds of Crime Act (POCA) in relation to the criminal property (e.g. imposing a restraint order). If the moratorium period expires and no such action has been taken, the reporter is free to proceed with the act(s) detailed in the initial disclosure.
44.4 It is company policy that all requests for consent must be processed through the company MLRO – it is expressly forbidden for employees to make a ‘consent’ request direct to NCA.
45. TIPPING OFF
45.1 Any staff member needs to make a judgement as to whether any delay to the transaction (‘consent request’) would have the effect of ‘tipping off’ the customer.
45.2 It is a criminal offence under POCA Part 7 for anyone, following a disclosure to the MLRO or to NCA, to do or say anything that might either ‘tip off’ another person that a disclosure has been made or in any way prejudice an investigation. The Terrorism Acts contain similar offences. This means that businesses must not tell a customer:
• that a transaction was/is being delayed because consent from NCA has been requested;
• that details of their transactions or activities will be/have been reported to NCA;
• that they are being investigated by law enforcement.
45.3 The punishment on conviction for ‘tipping off’ is a maximum of 5 years imprisonment or a fine or both.
45.4 In situations where delaying a transaction may inadvertently lead to ‘tipping off’, it will make sense to process the transaction and then ensure that a SAR is submitted to the MLRO as soon as possible after. The staff member will have the protection of the law as soon as a SAR has been submitted to the MLRO.
45.5 If in doubt about whether to proceed with a transaction, the staff member should call the MLRO for advice.
45.6 Processing subsequent transactions for a customer where a SAR has been filed to NCA.
45.7 These are situations where ‘enhanced due diligence’ is called for. Where a SAR has been made to NCA, the company will await to see if any response is received from NCA to the SAR which has been filed.
45.8 In the event that no response has been received from NCA on the previously reported transaction, then the MLRO will have to decide how to deal with the customer if he returns to process a subsequent transaction.
45.9 The MLRO may decide either:
• To refuse the transaction
• To process the transaction (but only having asked for written proof of source of funds to be provided) The MLRO has put in place a system to monitor customers where a report has been made to NCA. The MLRO will be able to identify and freeze transactions processed by customers who have previously been reported to NCA.
46. DECLINATURE OF SUSPICIOUS TRANSACTIONS
46.1 Agents must decline suspicious transactions (those transactions that qualify as such pursuant to the result of an analysis of money laundering risk carried out by the Staff / Agent), If this was not possible or was likely to frustrate the investigation, there is an urgent reporting duty to NCA via Hirett’s MLRO.
PART G. AML RECORD KEEPING
47. RESPONSIBILITY FOR AML RECORDS AND SAR FILING
47.1 Hirett’s Compliance Officer and his or her designee will be responsible to ensure that AML records are maintained properly and that any SARs are filed as required.
48. RECORD KEEPING AND CUSTODY OF DOCUMENTS
48.1 The UK AML regulations provide that records must be retained for 5 years from the date on which the first transaction was completed or declined.
48.2 Hirett’s cloud based system automatically keep this record once uploaded by Staff / Agent.
48.3 Agents must keep a copy of the customers’ identification documents, as well as those documents supporting the CDD measures. Documents will be kept on individual customer profiles maintained in Hirett cloud-based software.
48.4 The record-keeping procedure must identify the individuals in charge of the task. As according to the law, the company will keep full detailed records of all transactions with copies of identifications and proof of address provided by the customer. All customer records will be retained at least for a period of 5 (five) years from the date of the customer’s last transaction.
48.5 The company will also retain all bank statements, internal and external SAR’s as well as all records of training and compliance monitoring. All these records will likewise be kept for 5 (five) years.
49. SAR MAINTENANCE AND CONFIDENTIALITY
49.1 You should hold SARs and any supporting documentation confidential.
49.2 You should not inform anyone outside of a law enforcement or regulatory agency about a SAR.
49.3 You should refuse any subpoena requests for SARs or SAR information and immediately inform NCA of any such subpoena you receive.
49.4 You should segregate SAR-filings and copies of supporting documentation from other Company books and records to avoid disclosing SAR filings.
49.5 The AML Compliance Officer will handle all subpoenas or other requests for SARs.
PART G. STAFF AWARENESS AND TRAINING
50. TRAINING REQUIREMENT
50.1 Hirett follows training requirements set in PSRs 2017 to take appropriate measures so that all relevant employees are:
• Made aware of the law relating to money laundering or terrorist financing, and
• Regularly given training in how to recognize and deal with transactions and other activities which may be related to money laundering or terrorist financing.
50.2 Nominated Officers/MLROs, senior managers and others involved in ongoing monitoring of business relationships and other internal control procedures will need different training, tailored to their particular functions.
51. WHAT THIS TRAINING COVERS?
51.1 Hirett ensures that all staff and employees are made aware of their responsibilities under the Proceeds of Crime Act and the Terrorism Act to report knowledge or suspicion to the Nominated Officer and the requirements under Money Laundering Regulations for the business to apply customer due diligence measures.
TRAINING ENABLES EMPLOYEES AND STAFF TO RECOGNIZE AND DEAL WITH SUSPICIOUS TRANSACTIONS INCLUDES:
• the identity and responsibilities of the MLRO
• the risks of money laundering and terrorist financing that the business faces
• the vulnerabilities of the business’s products and services
• the policies and procedures that have been put in place to reduce and manage the risks
• customer due diligence measures, and, where relevant, procedures for monitoring customers’ transactions
• how to recognize potential suspicious activity
• the procedures for making a report to the MLRO
• the circumstances when consent is to be sought and the procedure to follow
• Reference to industry guidance and other sources of information, for example, NCA,
52. TRAINING FREQUENCY
52.1 All the new employees and agents of Hirett will be trained on AML when they join the business.
52.2 There is an annual refreshment training on AML. Refresher trainings are also given in the event of new regulation come into force.
52.3 All customer-facing staff are given training in relation to recognizing and handling suspicious transactions.
52.4 These trainings also cover the knowledge and competence of staff to apply customer due diligence measures appropriately and in accordance with the business’s risk assessments of the products or services business offer.
52.5 As part of ongoing staff / agent training, they are made aware of changing behaviour and practices amongst money launderers and that financing terrorism.
PART H. REPORTING
53. REPORTING DUTIES
53.1 Staff and Agents doing Money Transfer / Money Exchange for the business have certain reporting duties, which will be complied with through the designated MLRO.
54. REPORTING SUSPICIOUS TRANSACTIONS:
54.1 Agents must report any suspicious transaction in connection with Money Transfer / Money Exchange. The report of suspicious transactions should be drafted in accordance with the form and terms as provided in the applicable PSRs 2017.
55. REGULAR REPORTING:
55.1 Staff and Agents must report cases via Hirett’s MLRO on a monthly basis where transactions have taken place with cash or monetary movements up to HMRC threshold (see Appendix 2).
55.2 Agents should have appropriate annual training programmes to ensure that relevant staff are aware of the basic requirements of UK AML regulations and the UK section within their own AML internal policies. Level of compliance should be annually documented.
PART G. THE PROCESS FOR AUDITING THE FIRM’S COMPLIANCE WITH ITS POLICIES AND PROCEDURES:
56. BUSINESS MONITORING
56.1 It is the responsibility of the MLRO to monitor all the activity of the business with particular reference to the potential financial crime risk. The MLRO will keep a close eye on the following criteria and provide a report to senior management when required.
56.2 The report is likely to include commentary on the following issues (in the case that there is no information to report, there should be a ‘nil return’ should be indicated):
• Confirmation that adequate CDD information is being collected and that on-going monitoring is taking place
• Summary data relating to complex or unusual transactions
• Number of internal consents/SARs received from staff members
• Number of SARs made to National Crime Agency (NCA) previously Known as Serious Organised Crime Agency
• Information on status of staff training within the company
• Confirmation that all business records have been stored
• Changes in the law/operating environment which are or will impact the business
• Changes in risk matrix effecting the business
• Contacts with the regulator Reports should normally be written.
56.3 The MLRO should indicate where there is action of the regulator, law enforcement or other agency which raises any potential issues for the business.
56.4 The MLRO will, as a matter of policy, submit an annual report to the board of directors.
57. AML COMPLIANCE AUDIT
57.1 Hirett is conducting a yearly Compliance Audit through Internal Compliance Team and / or External APCC recognised Compliance Firm [i.e Acumen Accountants and Global Compliance] to identify the compliance weakness and failures,
57.2 Compliance Audit team Report the problems and Findings to the board of Directors/Management. Management takes action on the basis of the report. If still any errors are unidentified which can be identified by NCA, Hirett will rectify them as well.
Appendix 1. KYC IDENTIFICATION REQUIREMENTS
Following checks should made on the ID evidence given:
1. Always ensure that the ID provided is original, photocopies are not accepted.
2. Check any photographs for true likeness.
3. Check the date of birth compared to the customer’s apparent age.
4. Compare spelling of names and addresses on different ID documents.
5. Check for the authenticity of the ID provided as there are lots of counterfeit passports, driving licenses any asylum seeker’s documents in circulation.
6. Verify all the documents are ‘current’ which means these are not older than three months. All documents with expiry dates (such as passports, driving licences and identity cards) must be in force as of the date of receipt.
Find below a list of some of the acceptable forms or documents as ID. Use only as guidelines and refer to customer services for further inquiries.
| ENTITY TYPE | EVIDENCE REQUIRED | NOTES |
| Individual (UK or EU resident) | Proof of Name and Identity
PRIMARY ID:
ACCEPTABLE PROOF OF ADDRESS INCLUDES:
|
|
| Individual (Non-UK or EU resident) | Proof of Name and Identity
PRIMARY ID:
ACCEPTABLE PROOF OF ADDRESS INCLUDES:
|
Hirett follows industry standard upon checking customers immigration status. |
| Companies |
|
Appendix 2. CDD THRESHOLDS & SOF REQUIREMENTS
As per HMRC threshold requirements, CDD applies to a series of transactions totalling €15,000 or more or where there appears to be a link between transactions (linked transactions).
Hirett has further simplified overall thresholds requirement into smaller road blocks so that we are fully compliant with the requirement.
Hirett’s system automatically checks these thresholds (into GBP equivalent so we stay below threshold limit due to exchange rate buffer. e.g; €15,000 = £ 13,573.99 Approx. *GBP / Euro rates can vary on daily basis.) every 90 days and request KYC / CDD documentation based on the threshold standing.
| MONEY TRANSFER BUSINESS | ||
| AMOUNT | INFORMATION REQUIRED | KYC / CDD |
| £ 0 | Stage 1: Establishing a new Business Relationship
|
CDD Applies |
| £ 0 – £7,500 | Stage 2: Established on-going Business Relationship
|
|
| £7,500 + | Stage 2: Established on-going Business Relationship, Threshold evaluated regularly every 90 days
|
|
| CURRENCY EXCHANGE BUSINESS | ||
| AMOUNT | INFORMATION REQUIRED | KYC / CDD |
| £ 0 | Stage 1: Establishing a new Business Relationship
|
CDD Applies |
| £ 0 – £5,000 | Stage 2: Established on-going Business Relationship
|
EDD Applies |
| £5,000 – £10,000 | Stage 2: Established on-going Business Relationship, Threshold evaluated regularly every 90 days
|
|
| £5,000 – £10,000 | Stage: New Customer / One-off Transaction
|
|
| £14,500 + | Stage 3: Established on-going Business Relationship, Threshold evaluated regularly every 90 days
|
|
Appendix 3. Hirett – Flow of Funds
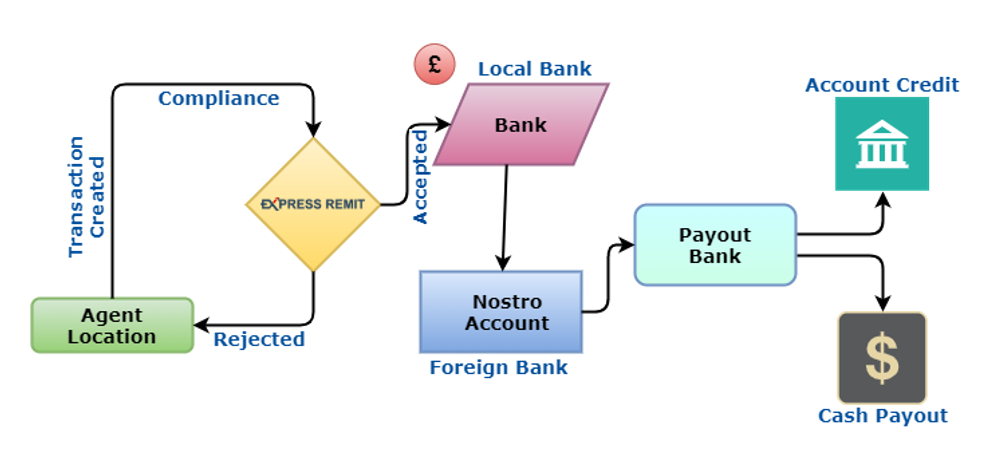
Appendix 4. System Generated SOF From – Sample
Stage 1: Once customer reaches any threshold limit (See Appendix 2), Staff / Agent see this message when they try to make a new transaction, they have to upload Source of Funds document along with the Declaration Form (Stage 2) for system to carry on with the transaction.
Stage 2: Below is system generated form needs to be uploaded with SOF documentation.
Appendix 5. Hirett – SAR (SAMPLE)
This form is part of e-SAR system but printable version can also be downloaded within Hirett system.
|
SUSPICIOUS ACTIVITY REPORT FORM |
INTERNAL SAR NUMBER: _______________
| PARTICULARS | REMARKS |
| Date: | |
| ID of the customer: | |
| Agents Name: | |
| Name/address of Customer: | |
| Telephone no of Customer: | |
| Nature of suspicious activity: | |
| Give full detail of suspicion:
[Include detail of transactions and identity checks.] |
|
Attach any relevant documents:
|
__Yes __No |
| Name of the Reporting Officer: | |
| Signature by Reporting Officer: | |
| Refer to NCA: [To be completed by MLRO] | __Yes __No |
| Do not refer to NCA: Reason for decision: Details | |
| Signature by MLRO: | |
| Date referred to NCA: |
Approved By: ……………………………………
Mr. Ray Allan
MLRO, Hirett
Appendix 6. Sources
- https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/889077/UTF-8__Guidance-for-Money-Service-Businesses-HM-Treasury-approved.docx_.pdf